The Journey from Suspicious URL to Malware Infection
Note: Please bear in mind that this is my first time publishing an analysis like this, and there may be mistakes. Therefore, please let me know if any facts are incorrect so that they can be corrected.
Introduction#
This originated from a Microsoft Defender for Endpoint alert, where it was identified as a threat actor on one endpoint. The threat actor is labelled as Storm-1113. According to Microsoft, Storm-1113 is a group in-development, and with that we have limited information at this time. the source delivery for the URL is unknown, but I believe it was from a potential Phishing email.
Initial Analysis#
It all starts with a newly registered domain that attempts to impersonate Zoom, a video calling application.
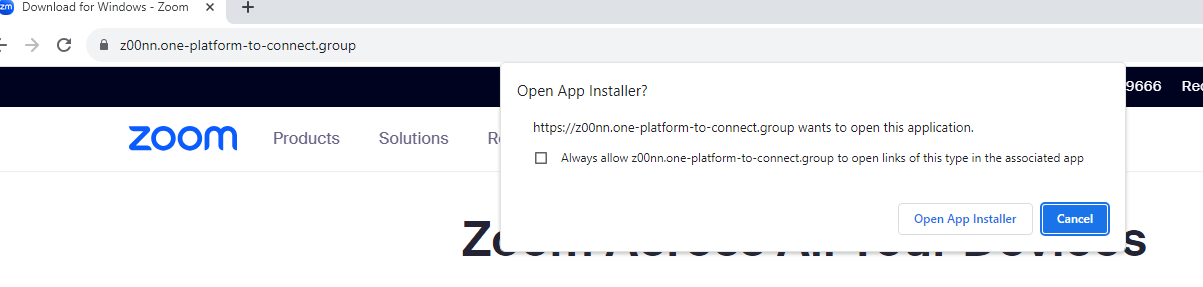
Upon visiting the domain I could see it was hosting a website, I encountered a glowing button in the centre with the text “Download Now”. Out of curiosity, I clicked on it. Using my Sandbox, I attempted to download the sample file to be analysed, but to be greeted with (MSIX file) Microsoft App Installer.
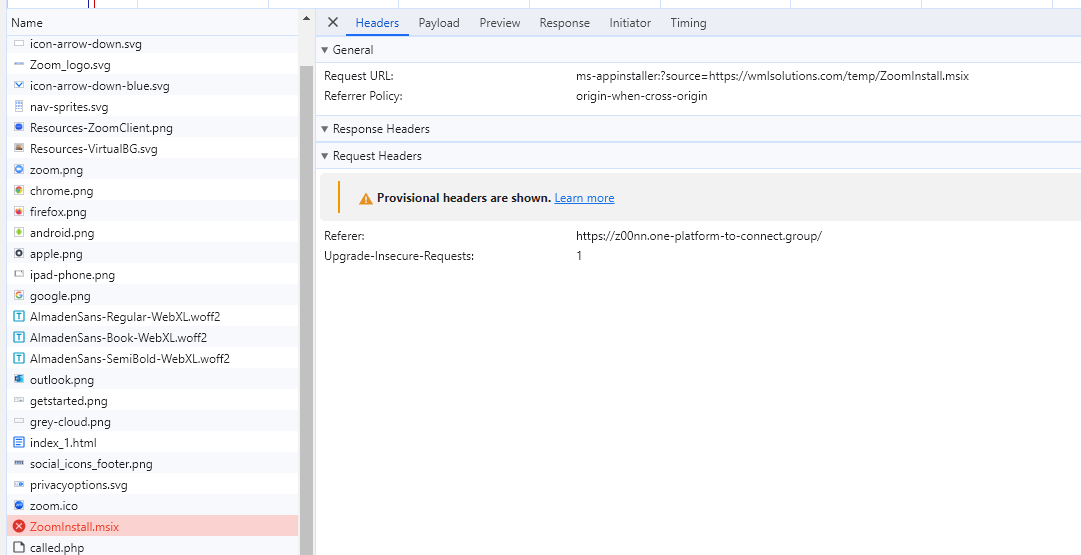
So instead of allowing the app installer to directly install and launch all files within the packed MSIX bundle from the web, I wanted to find an alternative way to download the file. Therefore, I decided to use Inspect Element to capture network traffic and identify the malicious file and its hosting location. As anticipated, I discovered that the file, labeled as “zoominstall.msix,” was hosted at
| |
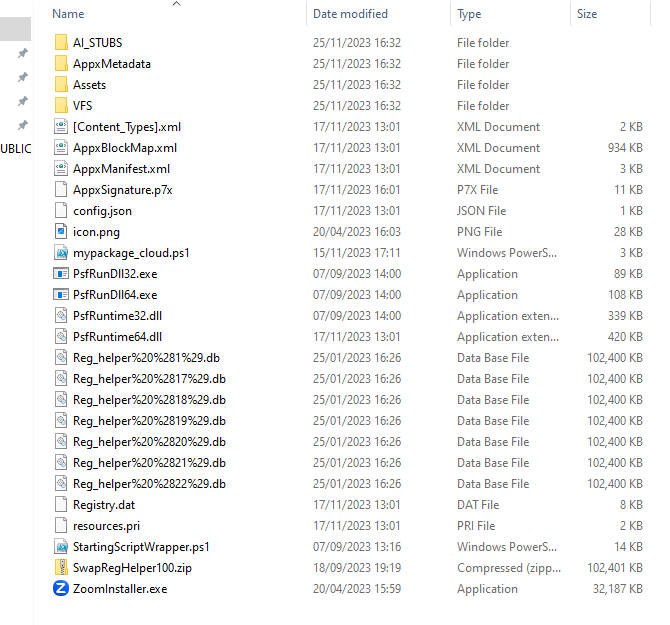
With the file located, I downloaded it using ‘Invoke-WebRequest’ within PowerShell to pull down the file. Then, I unpacked it using zip and we can see what is inside. As you will notice, there are plenty of different files, but the one thing that caught my eye early on was the PowerShell script “mypackage_cloud.ps1”.
Code Analysis#
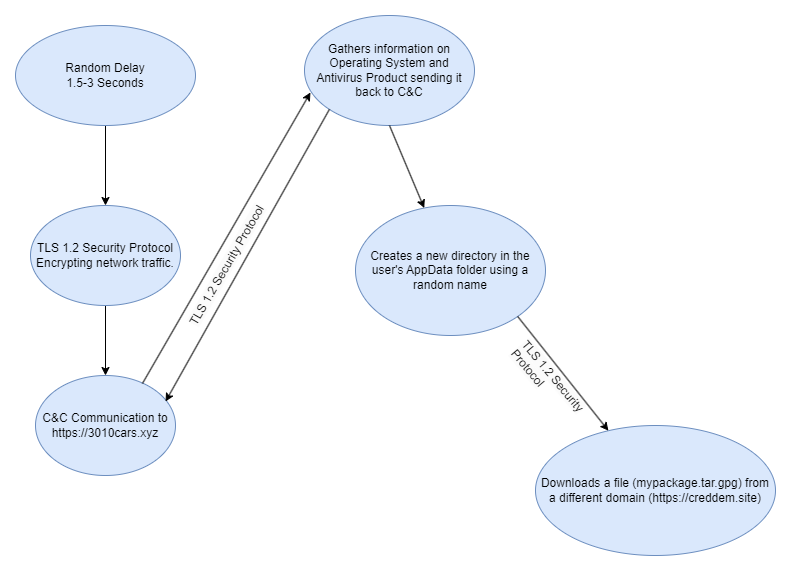
Upon my first glance, I noticed a few things. The first was ‘SecurityProtocol’. This appears to be creating the protocol to encrypt the network traffic. Therefore, if there is any outbound and inbound communication, it encrypts the network traffic using TLS 1.2.
| |
The first half of the script that was observed collecting information about the operating system and antivirus products. This part of the script was used for the initial command and control (C&C) connection under the following domain: ‘https[:]//3010cars[.]xyz’.
The second stage of the script is where the dropper is executed. We can see that the script invokes a web request to the following URL, from which it pulls down the malicious payload and places it into the user’s APPDATA folder.
| |
After the download is complete, the script proceeds to decrypt the file using a tool (gpg.exe) included in the ‘Zoominstall.msix’ file under the ‘VFS’ folder. It decrypts the file using the following parameters:
-batch: Non-interactive mode-yes: This option is used to assume “yes” on all prompts-passphrase-fd 0: GPG to read the passphrase from file descriptor 0,-decrypt: This specifies that the operation to be performed by GPG is decryption.-output $env:APPDATA\$xxx.rar: After decryption, this option specifies the output file for the decrypted data
| |
Below, I have created a graph to illustrate the flow of behaviour from start to finish before the final stage execution.
Dynamic Analysis#
So, for dynamic analysis, I decided to use Joe Sandbox. As I am still learning and put this together in a short time period, this would give me a full picture of what I am looking for at a faster rate, especially now that we have the final payload decrypted and unzipped we can upload the file and have it analysed. Joe Sandbox Analysis.
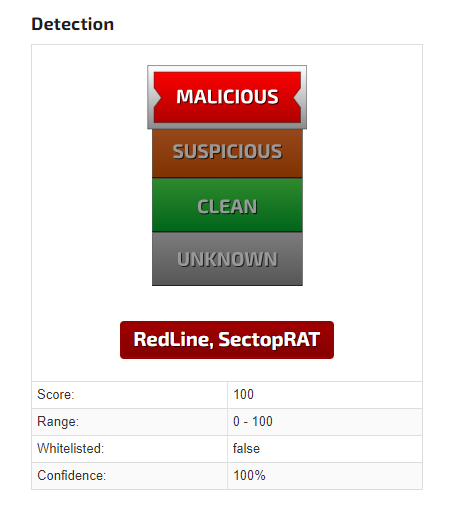
With the analysis complete, we can finally see that the malware has been identified as RedLine and SectopRAT, also known as ArechClient. We have also discovered that the delivery method has been idetified as GhostPulse downloader as per some analysis from Elastic Security team.
MITRE Attack Matrix#
References#
- https://jbxcloud.joesecurity.org/analysis/3488148/0/html - Dynamic Analysis
- https://learn.microsoft.com/en-us/windows/msix/app-installer/installing-windows10-apps-web
- https://www.elastic.co/security-labs/ghostpulse-haunts-victims-using-defense-evasion-bag-o-tricks
Indicators of compromise#
- Domain: z00nn.one-platform-to-connect[.]group
- Domain/URL: https://wmlsolutions[.]com/temp/ZoomInstall.msix
- ZoomInstall.msix - 97ac460432d117ab7d17d551f2fb2c0756dcaf3facfabe5dad4498a15903b935(SHA256)
- mypackage_cloud.ps1 - 07462f417aeee806059c798c829ba0bbe39add64322ff467a622df94d3987adf(SHA256)
- https://3010cars[.]xyz (Note: used as a call back to identify OS and AV information)
- https[:]//creddem[.]site/order/mypackage.tar.gpg